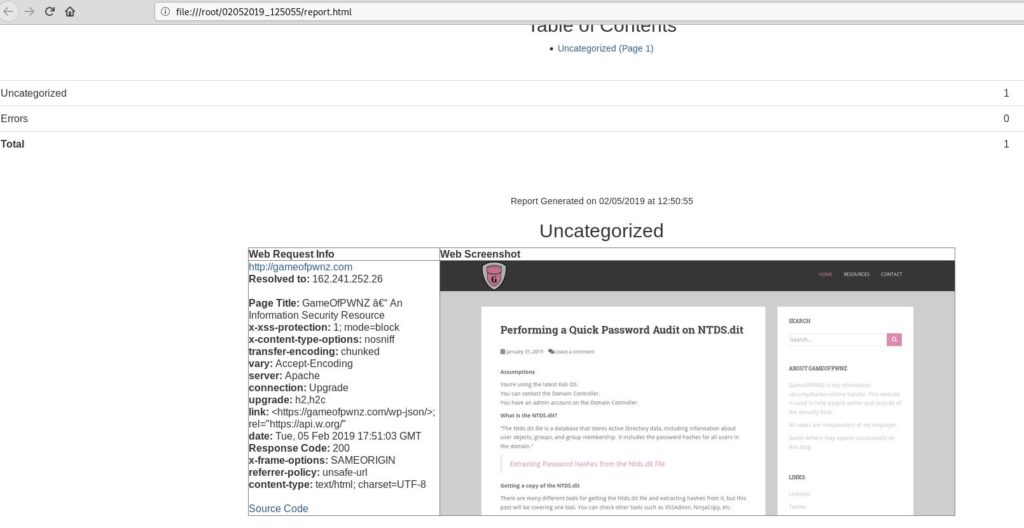
EyeWitness
“EyeWitness is designed to take screenshots of websites, RDP services, and open VNC servers, provide some server header info, and identify default credentials if possible.”
https://tools.kali.org/information-gathering/eyewitness
Assumptions:
You’re using Kali Linux
Downloads:
Setup
root@kali:/opt# git clone https://github.com/FortyNorthSecurity/EyeWitness.git
root@kali:/opt# cd EyeWitness/setup
root@kali:/opt/EyeWitness/setup# ./setup.sh
Using a file with hosts (-f)
root@kali:/PATH/TO/HOSTSFILE# python /opt/EyeWitness/EyeWitness.py -f hosts.txt --web
Using an nmap xml file (x)
root@kali:/PATH/TO/NMAP/SCANS# python /opt/EyeWitness/EyeWitness.py -x nmapscan.xml --web
If you want to add more http or https ports, you can use the following:
--add-http-ports 9000, 9001-add-https-ports 9002, 9003
Extra!
You can perform an active scan which will search for common locations of login forms and attempt to use common credentials against those web applications.
--active-scan
Example Output