Let’s give some starter information.
- 1Password said the vulnerability was not in scope on BugCrowd.
- 1Password said that some researchers have already reported this vulnerability.
- Bug was reported on Sunday, October 14, 2018.
- AgileBits responded on Wednesday, October 17, 2018. There is currently no fix or signs of them fixing the issue.
- Jake Miller (Laconic Wolf) reported a similar vulnerability on Dashlane (https://laconicwolf.com/2018/07/24/password-manager-vulnerability-dashlane/)
GameOfPWNZ identified a vulnerability in the 1Password Windows application. The application leaves passwords including the master password in memory even after the 1Password application has been locked.
GameOfPWNZ signed up for the 1Password Trial located here: https://1password.com/sign-up/
To exploit this vulnerability, an attacker would need to compromise the host machine that the application is on. The application must have been signed into and locked without a reboot to the host machine.
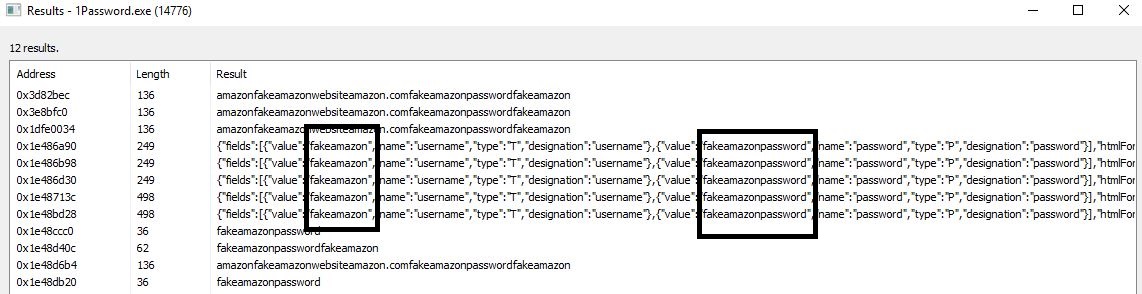
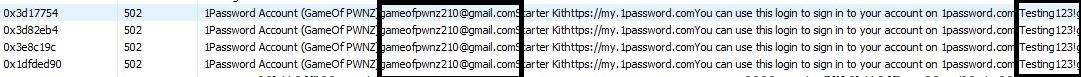
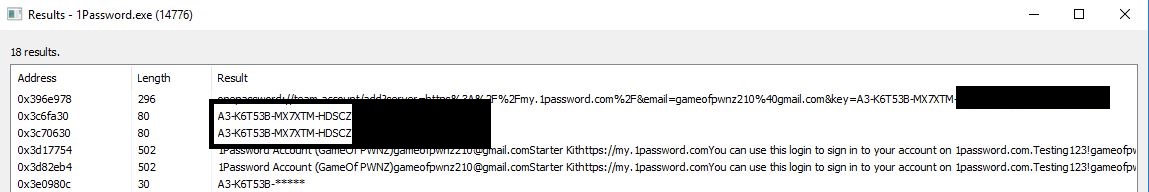
The below screenshots show GameOfPWNZ using Process Hacker to check memory for the process 1Password. The 1Password application was unlocked after system bootup (as a user would do) and used for one of the passwords. The application was then locked and was not unlocked for the rest of the testing (2-3 hours). After about 2-3 hours, GameOfPWNZ checked the memory and was able to obtain the master password as well as the password used during the earlier session.
Steps to Reproduce
- Login to 1Password Windows Application.
- Use normally
- Lock 1Password Windows Application.
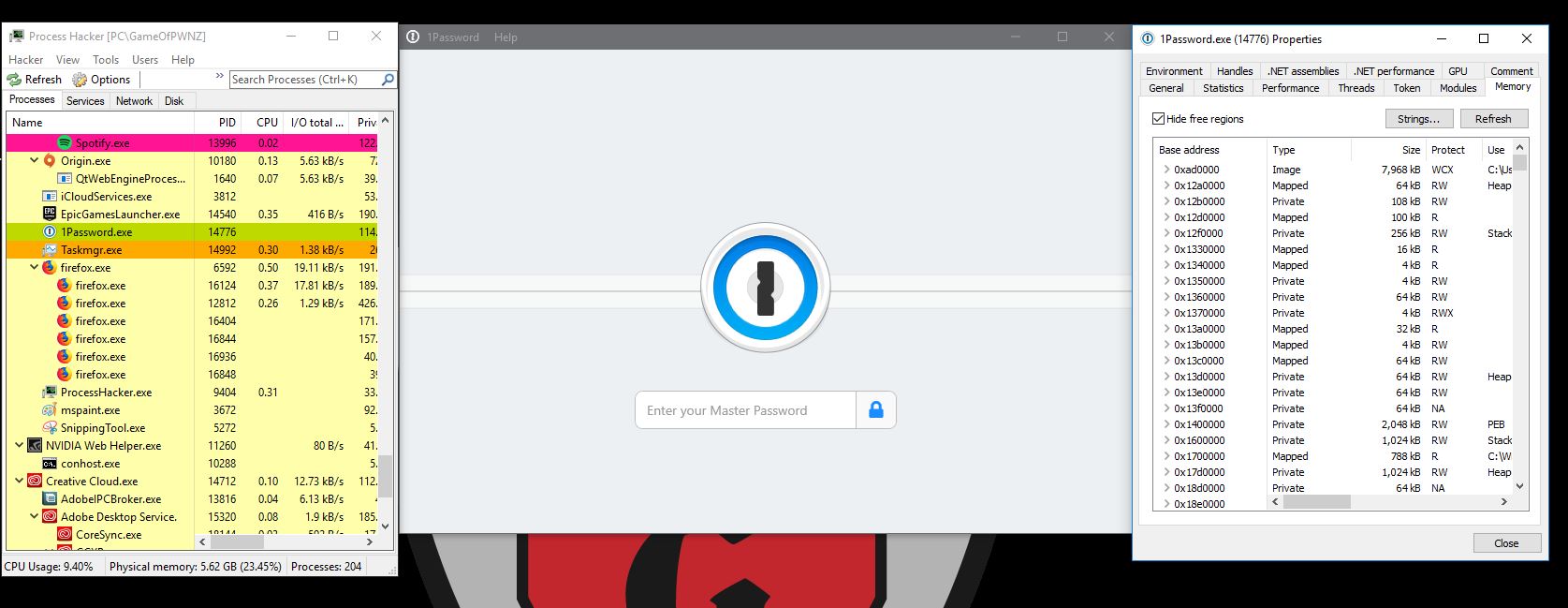
- Load Process Hacker
- Right click 1Password.exe and go to Properties.
- Go to the “Memory” tab.
- Click on the “Strings…” button.
- Keep defaults and press OK.
- Click on Filter.
- Select Contains.
- Enter password to search for (use master password if you want to see master password).
Notes: Host compromise is required. Think about how many users are local admin. My opinion is that this is an issue because a host compromise leads to compromise on social media, banking, etc. I think that wiping the memory after locking the application would be a good remediation for this issue.